The espionage business has never been like a James Bond flick, but these days it's probably the exact opposite. Modern day spies don't even leave their hometowns when out on the job and go to the office and sit in front of a computer all day, just like the rest of us.
A couple of years ago, Google made quite a fuss when it revealed that it had been the target of a very sophisticated attack and that dozens of other big American companies had been targeted and compromised.
Google didn't go as far as accuse the Chinese government of being behind the attack, but said it originated in China and that strategic companies in the US were targeted. The attack was a big part of the reason why Google decided to get out of China.
Not so much, a new report by Symantec, incidentally one of the companies targeted in the original attacks, revealed, the group has been very active to this day and continues to mine American companies for secrets.
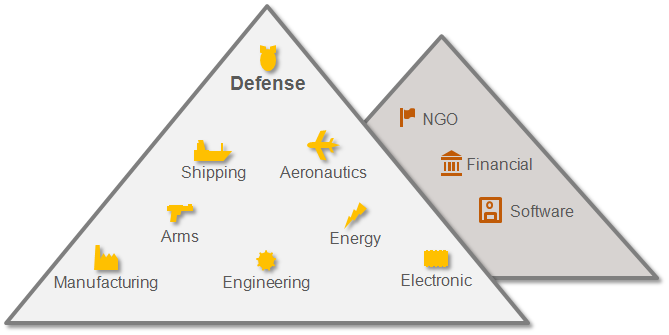
The hackers are focusing on industrial espionage in particular, anything they can steal they do. Areas targeted include defense, shipping, aeronautics, arms, energy, manufacturing, engineering, electronic and so on.
 |
The group has a seeming unlimited supply of zero-day vulnerabilities they sit on and use as needed. When one gets discovered or patched, they drag up the next one without pause. There aren't that many groups in the world capable of pushing a new zero day at will.
The Symantec researchers believe there is a dedicated team of skilled programmers that have reversed engineered the programs targeted or, alternatively, that have access to the source code of these programs.
Apparently, the new preferred method of gaining access to the companies targeted is the water hole attack. Unlike the common spear phishing attacks that are popular when dealing with highly targeted hacks, the water hole method relies on those targeted coming to the trap themselves.
A site that is known to be visited by many of the people in the organization targeted is hacked and infected using any number of zero day exploits. When the victims come in, vulnerabilities in Internet Explorer, Flash or whatever else is available, are exploited and a backdoor Trojan is installed, ensuring access to the internal network.
Via: Chinese Hacker Spies Behind Google Attack Sitting on Endless Supply of Zero-Days
Tidak ada komentar:
Posting Komentar